SPONSORED CONTENT — The modern battlefield has seen a transformation in the visibility of military and intelligence operations. To be “seen” or “not seen” is often the differentiator between success and failure, driving operations into the shadows. Increasingly, the same is true for transnational crime, illicit payments, sanctions-busting and criminal activity.
From Russian ransomware gangs to North Korean hackers, threat actors have looked to cryptocurrencies for revenue generation, money laundering, sanctions evasion and other illicit activity. Many of these actors perceive blockchain-based transactions to be protected from the prying eyes of regulators or law enforcement; especially for cross-border transactions. However, the reality is quite the opposite. Public blockchain technology is designed to be a trusted method for transactions explicitly because every transaction is published and available to everyone on the blockchain. Law enforcement, counter-terrorism, counter threat-finance and national security agencies worldwide are able to harness the power of blockchain technology to track and trace the flow of funds in ways impossible in the traditional world.
As we move further into a world where conflict and competition are fought – at least in part –on blockchains, it is critical to understand how cybercriminals, sanction-violators and nation state actors use blockchains to move crypto-currencies and other digital assets.
The native properties of public blockchains – data that is transparent, traceable and permanent – enables government agencies to leverage “blockchain intelligence” to identify risks more readily and more effectively in order to take action against illicit actors. Not unlike conventional battlefield intelligence, the tools of blockchain intelligence capture threat activity, threat intent and threat vulnerabilities. Through this advantage, regulators, special operators, sanction-enforcers and law enforcers can disrupt threat actors on the digital battlefield.
This is sponsored content. Consider publishing your national security-related, thought leadership content in The Cipher Brief, with a monthly audience reach of more than 500K national security influencers from the public and private sectors. Drop us a note at [email protected].
What is Blockchain Intelligence?
Also known as “blockchain analytics,” blockchain intelligence analyzes raw blockchain data in order to surface insights and risk indicators. It allows law enforcement and national security agencies unprecedented visibility into real-time financial flows. The nature of blockchain technology — the open and distributed ledger upon which tokens can be sent — means that each transaction is verified and logged in a shared, immutable record, along with the timestamp of the transaction and the addresses involved. This data can be used to understand connections between on-chain addresses, and can also be paired with off-chain intelligence to identify links to real-world entities. Illumination of financial flows through Blockchain Intelligence not only includes blockchain records, but sets the stage for expanded identification of threat actors who are hiding in plain sight.
State Actors, National Security Threats, and Cryptocurrencies; Deadly Combinations
The viability and value of blockchain intelligence can be readily seen in terrorist activity, sanctions-violations and law enforcement activities; but the blockchain ecosystem also harbors bigger prey. Increasingly, state actors have made use of blockchain technology for sanctions evasion, weapons proliferation, cybercrimes and other destabilizing activity. No nation state has attempted to exploit vulnerabilities within the crypto ecosystem as effectively as North Korea.
North Korea Continues to Attack the Crypto Ecosystem
Hackers tied to North Korea stole approximately USD 700 million in cryptocurrency in 2023, according to TRM Labs. North Korea was responsible for almost a third of all funds stolen in crypto attacks last year, despite a 20% reduction from the USD 850 million haul in 2022. Hacks perpetrated by North Korea were on average ten times as damaging as those perpetrated by other actors. Nearly USD 3 billion worth of crypto has been lost to North Korean threat actors since 2017.
OFAC has used sanctions to target cryptocurrency mixers and other services that North Korea has used to launder hacked funds. Cryptocurrency mixers are services that obfuscate transactional information, allowing users to obscure their connection to certain cryptocurrencies. While mixers are used for lawful purposes, North Korea has used them at scale to launder funds. However actions against mixers such as Tornado Cash and Sinbad demonstrate the ability of national security agencies to target the services used by North Korea to launder hacked and stolen funds.
For example, in March 2022, Lazarus Group struck the Ronin bridge, a service that allows users to move funds from one blockchain to another, stealing over $600 million in cryptocurrency that could potentially be used by North Korea for weapons proliferation and other destabilizing activity. What followed was OFAC using blockchain intelligence to trace the stolen funds sanctioning both the blockchain addresses to which the funds moved, and the mixing services that North Korea utilized to launder the proceeds – including centralized bitcoin mixer blender.io and decentralized Ethereum mixer Tornado Cash. These rapid sanctions designations were only possible because of the transparent nature of public blockchains.
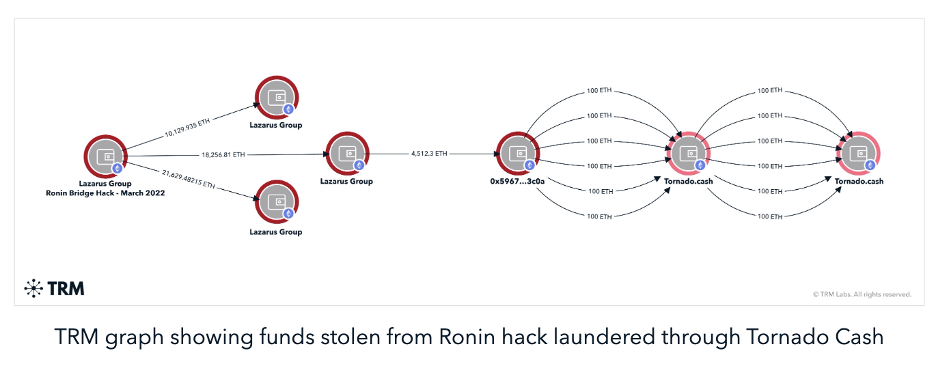
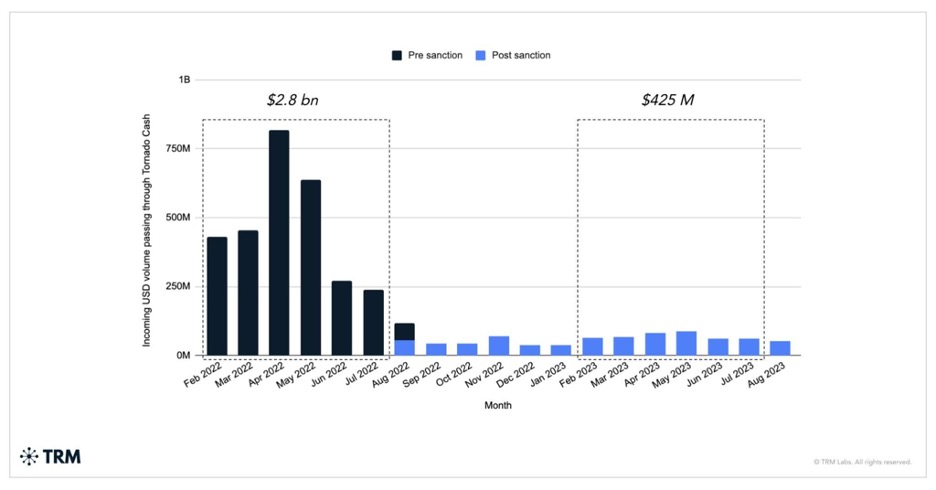
OFAC’s sanctioning of Tornado Cash succeeded in radically reducing usage of the service. According to TRM, the overall volume passing through Tornado Cash decreased by close to 85% post OFAC sanctions. Perhaps most importantly, North Korean hackers appear to have largely abandoned the service in favor of more traditional Bitcoin mixers. With nearly USD 1.5 billion stolen in the past two years alone, North Korea’s hacking prowess demands continuous vigilance and innovation from business and governments.
Looking for a way to get ahead of the week in cyber and tech? Sign up for theCyber Initiatives GroupSunday newsletter to quickly get up to speed on the biggest cyber and tech headlines and be ready for the week ahead. Sign up today.
Terrorist groups have looked to crypto as one piece of financing puzzle
Particularly following the Hamas attacks on Israel in October 2023, the use of cryptocurrency by international terrorist groups has taken on renewed urgency among governments, policymakers and researchers. And while cash, hawala and even traditional money services remain the default tools for terrorism financing, TRM research found a growing interest in and use of crypto by terrorist groups and their supporters. Nevertheless, to date cryptocurrency use (especially as it relates to fundraising campaigns) appears to be primarily confined to small-scale transactions of under USD 100. Three-quarters of donations to terrorist fundraising campaigns were under USD 500, with around 40% at USD 100 or less.
While the overall volume remains relatively low, in recent years, terrorist groups and their supporters have used cryptocurrency – more recently using the stablecoin Tether (USDT) on the TRON (TRX) blockchain – to solicit donations and conduct cross-border payments. This includes ISIS and its affiliates in multiple countries around the world, as well as Iranian-backed groups like Hamas and Palestinian Islamic Jihad (PIJ), which have received hundreds of thousands of dollars’ in cryptocurrency over the past few years.
However, in 2023 Hamas and or sympathetic fundraising campaigns received only modest amounts of crypto, possibly due to the successful targeting of these accounts by Israeli authorities and private sector agencies. Indeed, Hamas announced last year that it would no longer accept cryptocurrency donations.
This could be related to the successful targeting by US and Israeli authorities. Over the last few years, Israel’s National Bureau for Counter Terror Financing (NBCTF) has repeatedly targeted Hamas’ use of cryptocurrency, seizing dozens of cryptocurrency addresses with tens of millions of dollars in volume, controlled by entities affiliated with Hamas. For example, on October 10, 2023, the cyber branch of the Israel Police’s Lahav 433 announced the seizure of cryptocurrency accounts belonging to Hamas and in July 2021, the NBCTF released a copy of an administrative seizure for Bitcoin, Dogecoin, TRON, and other cryptocurrency addresses controlled by agents of Hamas.
In December 2022, TRM’s blockchain intelligence platform identified an address controlled by Shamil Hukumatov. Turkish authorities alleged that the Tajikistan national worked to recruit Tajiks to join the ISIS affiliate in Afghanistan, known as the Islamic State in Khurasan (ISKP or ISIS-K) and launch attacks against the Tajik government. TRM Labs notified Binance, the exchange used by the group to cash out some of their funds. Using know-your-customer (KYC) controls, Binance’s compliance and financial crime teams identified the person operating the account and alerted the local authorities. The information led to the arrest of two individuals in Tajikistan in April 2023. Turkish authorities arrested Hukumatov two months later.
It’s not just for the President anymore. Are you getting your daily national security briefing?Subscriber+Members have exclusive access to theOpen Source Collection Daily Brief, keeping you up to date on global events impacting national security. It pays to be a Subscriber+Member.
Darknet markets and non-compliant exchanges fuel Russia’s money laundering state
Russia has long been a haven for money launderers, ransomware gangs, and darknet markets. This activity has been facilitated by non-compliant cryptocurrency exchanges, OTC brokers, and networks of facilitators who move funds using cryptocurrencies and other methods for Russian elites in order to evade ever-expanding sanctions. However, law enforcement and national security agencies are targeting Russia-linked ransomware networks. For example, on February 20, 2024, the UK’s National Crime Agency, the US Department of Justice, the FBI, and Europol announced the disruption of LockBit and the takedown of its associated website infrastructure. In addition, the US Treasury Department’s Office of Foreign Assets Control (OFAC) designated two Russian nationals for their involvement as LockBit affiliates.
Through on-chain analysis, TRM estimates that addresses controlled by LockBit administrators and affiliates have received over GBP 160 million (USD 200 million) in bitcoin since 2022, of which over GBP 50 million (USD 63 million) are still unspent in multiple addresses on-chain.
Additionally, last year the U.S. Department of Justice and the U.S. Treasury Department announced a coordinated action against non-compliant Hong Kong-registered cryptocurrency exchange Bitzlato, for facilitating Russian illicit finance – particularly, ransomware and darknet markets — allowing Treasury’s Financial Crimes Enforcement Network (FinCEN) to issue for the first time an order pursuant to section 9714(a) of the Combating Russian Money Laundering Act.
Treasury’s strategy began to take shape in 2021 when it sanctioned Russia-based exchanges Suex, Chatex, followed by an action in 2022 against exchange Garantex for facilitating payments to Russian language darknet market Hydra.
Iran has turned to crypto to move funds in international trade
Even as both Iran and Russia have banned their residents from using cryptocurrencies for payments, these two governments have been working to establish crypto payments for foreign trade. Iran already announced its first official import order – worth $10 million – back in August 2022. Statements from Russia’s finance ministry’s financial policy department had already confirmed that Russia is exploring how to use crypto for international payments.
Most recently, in the wake of the October 7 attacks on Israel there has been a focus on the way that Iran funds terrorism. In January 2024, U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed sanctions on financial facilitators that have played key roles in funds transfers, including cryptocurrency transfers, from Iran’s Islamic Revolutionary Guard Corps-Qods Force (IRGC-QF) to Hamas and Palestinian Islamic Jihad (PIJ) in Gaza.
In addition, in February 2024, OFAC targeted individuals and entities involved in the government of Iran’s program to develop a Central Bank Digital Currency (CBDC).
What national security news are you missing today? Get full access to your own national security daily brief by upgrading to Subscriber+Member status.
Treasury has effectively targeted crypto-denominated fentanyl sales
Following a multi-year boom, crypto-denominated fentanyl dropped by over 150% in 2023 according to TRM Labs.
Despite the slowdown in growth, total volumes still grew by over 80% over 2023 from USD 16 million to USD 29 million. Moreover, such crypto-denominated sales likely represent a fraction of the total market for fentanyl and fentanyl precursors, most of which continue to be traded using traditional currency.
The decrease in the growth rates appears to correlate with significant sanctions and enforcement events: the US Treasury’s Office of Foreign Assets Control (OFAC) sanctioned 135 individuals and entities linked to fentanyl production and distribution across 12 designation events. That followed a steady increase in designation activity since 2018, with five individuals and entities designated in 2019, seven in 2020, 15 in 2021 and 17 in 2022 (see Sanctions section below).
It is impossible to ascribe any one cause to the decreased crypto-related fentanyl sales in 2023: other events, such as indictments by the US Department of Justice (DOJ), may have also contributed to the trend. However, OFAC’s actions are likely to have disrupted supplies by increasing the risks of engaging with targeted precursor manufacturers. As illicit actors continue to use cryptocurrencies for the illicit trade of fentanyl, law enforcement and national security agencies can use blockchain intelligence for sanctions, arrests and other disruptions.
Conclusion
National security, sanctions enforcement, counter-criminal and counter-terrorism success increasingly requires the tools and techniques to operate in new and evolving domains. As more and more transactions occur on blockchains, we will continue to see criminal and state actors look to take advantage of the promise of cryptocurrencies. The ability to investigate, seize, and disrupt those transactions is critical.
As illicit actors and nation states take advantage of emerging technologies, leveraging blockchain intelligence allows us to “see” threat actors even on the digital battlefield.
This is sponsored content. Consider publishing your national security-related, sponsored content in The Cipher Brief, with a monthly audience reach of more than 500K national security influencers from the public and private sectors. Drop us a note at [email protected].







